жӮЁеҘҪпјҢзҷ»еҪ•еҗҺжүҚиғҪдёӢи®ўеҚ•е“ҰпјҒ
# е°Ҷkeepalivedи§ЈеҺӢеҲ°/usr/localзӣ®еҪ•дёӢ
tar -zxvf keepalived-2.0.11.tar.gz -C /usr/localcd /usr/local/keepalived-2.0.11
./configure --prefix=/usr/local/keepalived
#зј–иҜ‘并е®үиЈ…
make && make install
еҮәзҺ°д»ҘдёӢдҝЎжҒҜиЎЁзӨәзј–иҜ‘жҲҗеҠҹKeepalived version : 2.0.11
Compiler : gcc
Preprocessor flags :
Compiler flags : -Wall -Wunused -Wstrict-prototypes -Wextra -Winit-self -g -D_GNU_SOURCE -fPIE -Wformat -Werror=format-security -Wp,-D_FORTIFY_SOURCE=2 -fexceptions -fstack-protector-strong --param=ssp-buffer-size=4 -grecord-gcc-switches -O2
Linker flags : -pie
Extra Lib : -lcrypto -lssl -lnl
Use IPVS Framework : Yes
IPVS use libnl : Yes
IPVS syncd attributes : No
IPVS 64 bit stats : No
HTTP_GET regex support : No
fwmark socket support : Yes
Use VRRP Framework : Yes
Use VRRP VMAC : Yes
Use VRRP authentication : Yes
With ip rules/routes : Yes
Use BFD Framework : No
SNMP vrrp support : No
SNMP checker support : No
SNMP RFCv2 support : No
SNMP RFCv3 support : No
DBUS support : No
SHA1 support : No
Use JSON output : No
libnl version : 1
Use IPv4 devconf : No
Use iptables : Yes
Use libiptc : No
Use libipset : No
Use nftables : No
init type : systemd
Strict config checks : No
Build genhash : Yes
Build documentation : No
зј–иҜ‘еҸҜиғҪеҮәзҺ°зҡ„й—®йўҳ
*** WARNING - this build will not support IPVS with IPv6. Please install libnl/libnl-3 dev libraries to support IPv6 with IPVS.
жү§иЎҢyumе‘Ҫд»Өyum -y install libnl libnl-develи§ЈеҶідёҠиҝ°иӯҰе‘Ҡй—®йўҳ
yum -y install libnl libnl-devel
configure: error: in /usr/local/keepalived-2.0.11':<br/>configure: error: no acceptable C compiler found in $PATH<br/>Seeconfig.log' for more details
yum install gcc
configure: error:
!!! OpenSSL is not properly installed on your system. !!!
!!! Can not include OpenSSL headers files. !!!
[root@dajia keepalived-2.0.11]#
yum -y install openssl-devel
е®үиЈ…е®ҢжҲҗд»ҘеҗҺпјҢйҮҚж–°жү§иЎҢconfigure ... е‘Ҫд»Ө
е°Ҷkeepalivedж·»еҠ еҲ°зі»з»ҹжңҚеҠЎдёӯ
и·Ҝеҫ„ иҜҙжҳҺ
/usr/local/keepalived-2.0.10 и§ЈеҺӢеҗҺжәҗз Ғеӯҳж”ҫи·Ҝеҫ„
/usr/local/keepalived е®үиЈ…зӣ®еҪ•
# жӢ·иҙқжү§иЎҢж–Ү件
cp /usr/local/keepalived/sbin/keepalived /usr/sbin/
# е°ҶеҲқе§ӢеҢ–и„ҡжң¬жӢ·иҙқеҲ°зі»з»ҹеҲқе§ӢеҢ–зӣ®еҪ•дёӢ
cp /usr/local/keepalived-2.0.10/keepalived/etc/init.d/keepalived /etc/init.d/
# е°Ҷkeepalivedй…ҚзҪ®ж–Ү件жӢ·иҙқеҲ°etcдёӢ
cp /usr/local/keepalived-2.0.10/keepalived/etc/sysconfig/keepalived /etc/sysconfig/
# еҲӣе»әkeepalivedж–Ү件еӨ№
mkdir /etc/keepalived/
# е°Ҷkeepalivedй…ҚзҪ®ж–Ү件жӢ·иҙқеҲ°etcдёӢ
cp /usr/local/keepalived-2.0.10/keepalived/etc/keepalived/keepalived.conf /etc/keepalived/
# ж·»еҠ еҸҜжү§иЎҢжқғйҷҗ
chmod +x /etc/init.d/keepalived
# ж·»еҠ keepalivedеҲ°ејҖжңәеҗҜеҠЁ
chkconfig --add keepalived
chkconfig keepalived on
жӯӨж—¶е·ІеҠ е…Ҙзі»з»ҹжңҚеҠЎ еҸҜдҪҝз”Ёservices еҗҜеҠЁ
#еҗҜеҠЁ
service keepalived start
#еҒңжӯў
service keepalived stop
#йҮҚеҗҜ
service keepalived restart
#жҹҘзңӢеҗҜеҠЁжғ…еҶө
ps -aux |grep keepalived
й…ҚзҪ®keepalivedиҷҡжӢҹIP
дҝ®ж”№еҲҡж·»еҠ еҲ°зі»з»ҹзҡ„й…ҚзҪ®ж–Ү件пјҡvi /etc/keepalived/keepalived.conf
жіЁж„Ҹ жҳҜзі»з»ҹзҡ„й…ҚзҪ®ж–Ү件(/etc/keepalived/keepalived.conf)
жіЁж„Ҹ жҳҜзі»з»ҹзҡ„й…ҚзҪ®ж–Ү件(/etc/keepalived/keepalived.conf)
жіЁж„Ҹ жҳҜзі»з»ҹзҡ„й…ҚзҪ®ж–Ү件(/etc/keepalived/keepalived.conf)
дёҚжҳҜе®үиЈ…зӣ®еҪ•/usr/local...дёӢзҡ„
vrrp_instance VI_1 {
state MASTER //MASTERдё»иҠӮзӮ№пјҢеӨҮз”ЁиҠӮзӮ№дёҠи®ҫзҪ®дёәstate BACKUP
interface ens33 //з»‘е®ҡиҷҡжӢҹжңәIPзҡ„зҪ‘еҚЎ дёӨдёӘиҠӮзӮ№и®ҫзҪ®дёҖж · ж №жҚ® ipaddrжҚўжҲҗеҜ№еә”зҡ„зҪ‘еҚЎең°еқҖ
virtual_router_id 51 //VRRPз»„еҗҚпјҢдё»еүҜиҠӮзӮ№и®ҫзҪ®еҝ…йЎ»дёҖж ·пјҢжҢҮеҗҚеҗ„дёӘиҠӮзӮ№еұһдәҺеҗҢдёҖдёӘVRRPз»„пјҢеҗҢдёҖдёӘз»„зҡ„иҠӮзӮ№дә’зӣёжҠўIP
priority 100 //дјҳе…Ҳзә§(1~254д№Ӣй—ҙ)пјҢеӨҮз”ЁиҠӮзӮ№еҝ…йЎ»жҜ”дё»иҠӮзӮ№дјҳе…Ҳзә§дҪҺ
advert_int 1 //з»„ж’ӯдҝЎжҒҜеҸ‘йҖҒй—ҙйҡ”пјҢдёӨдёӘиҠӮзӮ№и®ҫзҪ®еҝ…йЎ»дёҖж ·
authentication { //и®ҫзҪ®йӘҢиҜҒдҝЎжҒҜпјҢ дёӨдёӘиҠӮзӮ№и®ҫзҪ®еҝ…йЎ»дёҖж ·пјҢз”ЁдәҺиҠӮзӮ№й—ҙдҝЎжҒҜиҪ¬еҸ‘ж—¶зҡ„еҠ еҜҶ
auth_type PASS
auth_pass 1111
}
virtual_ipaddress { // иҷҡжӢҹIPдёӨдёӘиҠӮзӮ№и®ҫзҪ®еҝ…йЎ»дёҖж ·пјҢдёӨиҠӮзӮ№еҗҢж—¶жҠўдёҖдёӘio
192.168.33.60/24 // еҰӮжһңдёӨдёӘnginxзҡ„ipеҲҶеҲ«жҳҜ192.168.33.61,,...62пјҢеҲҷжӯӨеӨ„зҡ„иҷҡжӢҹipи·ҹе®ғдҝ©еҗҢдёҖдёӘзҪ‘ж®өеҚіеҸҜ 24д»ЈиЎЁ3дёӘ255зҡ„еӯҗзҪ‘жҺ©з Ғ
}
}
еҰӮжһңиҰҒ ping 192.168.33.60 иҝҳйңҖиҰҒжіЁйҮҠжҺүй…ҚзҪ®ж–Ү件дёӯзҡ„# vrrp_strict
йҒҮеҲ°зҡ„й—®йўҳ
дё»еӨҮйғҪжҠўеҲ°дәҶиҷҡжӢҹip
йҮҮз”ЁtcpdumpжҠ“еҢ…е®ҡдҪҚй—®йўҳпјҢд»ҘдёӢжҳҜеңЁ192.168.93.141 дё»иҠӮзӮ№зҡ„жҠ“еҢ…з»“жһң
tcpdump -i ens33 vrrp -n
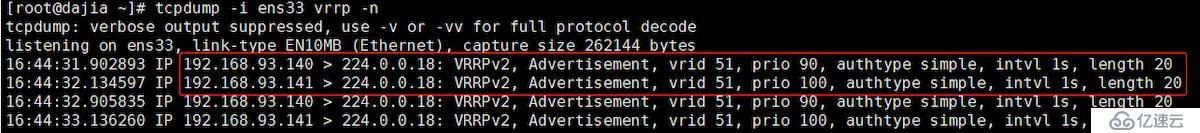
д»ҘдёӢжҳҜеңЁ10.11.4.187 еӨҮиҠӮзӮ№зҡ„жҠ“еҢ…з»“жһң
tcpdump -i ens33 vrrp -n
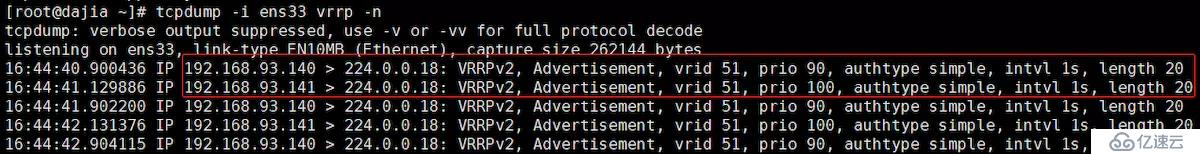
з”ұдёҠеӣҫеҸҜд»ҘзңӢеҲ°пјҢ192.168.93.140е’Ң192.168.93.141дёӨдёӘIPеңЁиҪ®жөҒеҸ‘йҖҒз»„ж’ӯдҝЎеҸ·гҖӮиҖҢжӯЈеёёзҡ„еә”иҜҘжҳҜз”ұMASTERжңҚеҠЎеҷЁеҸ‘йҖҒз»„ж’ӯпјҢеҰӮжһңBACKUP收дёҚеҲ°MASTERзҡ„з»„ж’ӯдҝЎеҸ·дәҶпјҢйӮЈд№ҲеҲӨе®ҡMASTERе®•жңәдәҶпјҢBACKUPе°ұдјҡжҺҘжүӢVIP
й—®йўҳе°ұжҳҜеҮәзҺ°еңЁдәҶйҳІзҒ«еўҷиҝҷйҮҢпјҢйҳІзҒ«еўҷйҳ»жӯўдәҶvrrpз»„еҢ…еҸ‘йҖҒ
еҰӮжһңжҳҜFirewalldйҳІзҒ«еўҷ еҲҷдё»гҖҒеӨҮйғҪиҝҗиЎҢдёӢйқўзҡ„е‘Ҫд»Ө
[root@dajia sysconfig]# firewall-cmd --direct --permanent --add-rule ipv4 filter INPUT 0 --protocol vrrp -j ACCEPT
success
[root@dajia sysconfig]# firewall-cmd --reload
success
е…ҚиҙЈеЈ°жҳҺпјҡжң¬з«ҷеҸ‘еёғзҡ„еҶ…е®№пјҲеӣҫзүҮгҖҒи§Ҷйў‘е’Ңж–Үеӯ—пјүд»ҘеҺҹеҲӣгҖҒиҪ¬иҪҪе’ҢеҲҶдә«дёәдё»пјҢж–Үз« и§ӮзӮ№дёҚд»ЈиЎЁжң¬зҪ‘з«ҷз«ӢеңәпјҢеҰӮжһңж¶үеҸҠдҫөжқғиҜ·иҒ”зі»з«ҷй•ҝйӮ®з®ұпјҡis@yisu.comиҝӣиЎҢдёҫжҠҘпјҢ并жҸҗдҫӣзӣёе…іиҜҒжҚ®пјҢдёҖз»ҸжҹҘе®һпјҢе°Ҷз«ӢеҲ»еҲ йҷӨж¶үе«ҢдҫөжқғеҶ…е®№гҖӮ
жӮЁеҘҪпјҢзҷ»еҪ•еҗҺжүҚиғҪдёӢи®ўеҚ•е“ҰпјҒ