您好,登录后才能下订单哦!
1.测试拓扑:
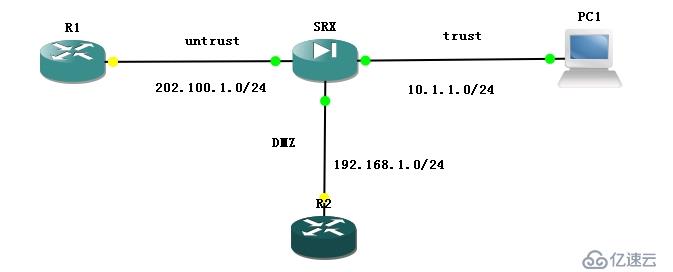
2.测试总结:
3.基本配置:
A.路由器R1:
interface Ethernet0/0
ip address 202.100.1.1 255.255.255.0
no shut
B.防火墙SRX:
①配置接口地址:
set interfacesge-0/0/0.0family inetaddress 202.100.1.10/24
set interfacesge-0/0/1.0family inetaddress 10.1.1.10/24
set interfacesge-0/0/2.0family inetaddress 192.168.1.10/24
②将接口划入zone:
setsecurity zones security-zone untrust interfacesge-0/0/0.0
setsecurity zones security-zone trust interfacesge-0/0/1.0
setsecurity zones security-zone dmz interfacesge-0/0/2.0
③配置zone间策略,允许trust到untrust的任何访问:
setsecurity policies from-zone trust to-zone untrust policy Permit-All match source-address any
setsecurity policies from-zone trust to-zone untrust policy Permit-All match destination-address any
setsecurity policies from-zone trust to-zone untrust policy Permit-All match application any
setsecurity policies from-zone trust to-zone untrust policy Permit-All then permit
④配置zone间策略,允许DMZ到untrust的任何访问:
set security policies from-zone dmz to-zoneuntrust policy Permit-All match source-address any
set security policies from-zone dmz to-zoneuntrust policy Permit-All match destination-address any
set security policies from-zone dmz to-zoneuntrust policy Permit-All match application any
set security policies from-zone dmz to-zoneuntrustpolicy Permit-All then permit
C.主机PC1:
IP:10.1.1.8/24
GW:10.1.1.10
D.路由器R2:
interface f0/0
ip address 192.168.1.2 255.255.255.0
no shut
ip route 0.0.0.0 0.0.0.0 192.168.1.10
4.NAT配置:
A.第一种NAT:
Source NAT:Interface NAT配置:
A.指定NAT的zone:
setsecurity nat sourcerule-set Source-NAT from zone trust
setsecurity nat sourcerule-setSource-NATto zone untrust
B.配置Interface NAT:
setsecurity nat source rule-set Source-NAT rule NAT-Interface match source-address 0.0.0.0/0
setsecurity nat source rule-set Source-NAT rule NAT-Interface match destination-address 0.0.0.0/0
setsecurity nat source rule-set Source-NAT rule NAT-Interface then source-nat interface
C.提交配置:
commit
D.验证:
从主机PC1上面ping路由器R1接口地址,并在R1上debug ip icmp,可以看到ICMP源地址为防火墙接口地址
R1#
*Mar 2 01:35:56.797: ICMP: echo reply sent, src 202.100.1.1, dst 202.100.1.10
*Mar 2 01:35:57.793: ICMP: echo reply sent, src 202.100.1.1, dst 202.100.1.10
*Mar 2 01:35:58.809: ICMP: echo reply sent, src 202.100.1.1, dst 202.100.1.10
*Mar 2 01:35:59.749: ICMP: echo reply sent, src 202.100.1.1, dst 202.100.1.10
R1#
B.第二种NAT:
Source NAT:pool based nat配置:
A.配置地址池:
set security nat source pool src-nat-pool1address 202.100.1.11 to 202.100.1.13
B.指定NAT的zone(前面已经配置,可以不配):
set security nat source rule-set Source-NAT from zone trust
set security nat sourcerule-set Source-NATto zone untrust
C.配置pool based nat:
set security nat source rule-set Source-NAT rule NAT-pool match source-address 0.0.0.0/0
sets ecurity nat source rule-set Source-NAT rule NAT-pool match destination-address 0.0.0.0/0
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。