您好,登录后才能下订单哦!
基础交换技术
本文将通过实验展示基础交换技术里面关键知识点,主要以实际配置&关键注意点为主,其基础概念不会作解释。
实验环境:
GNS3,三层交换机使用C3640+交换接口模拟,二层交换机使用C3640+交换接口+关闭路由功能模拟,DHCP服务器&主机使用C7200+关闭路由功能模拟
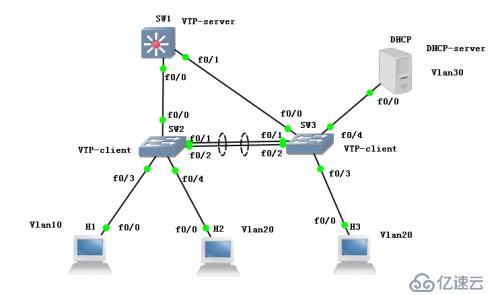
包含技术:
交换技术:VTP创建同步VLAN,划分VLAN,配置trunk
交换冗余技术:Etherchannel
交换防环&导流技术:STP
交换安全技术:port-security
交换通信技术:三层交换通信,DHCP
最终实现:
H1,H2,H3 IP地址均由DHCP下发对应的VLAN网段,VLAN间能相互通信;VLAN10流量走SW2-SW1主路线,备用路线SW2-SW3-SW1,VLAN20流量走SW2-SW3-SW1主路线,备用路线SW2-SW1,在链路故障时可以自动切换备用路线;SW2与SW3之间做链路冗余。
VLAN10网段为192.168.1.X 网关为1.254 VLAN20网段为192.168.2.X 网关为2.254 VLAN30网段为192.168.3.X 网关为3.254,网关均为SW1。
相关重点配置:
VTP配置并且创建同步vlan
SW1配置为server,其他SW与其同步
SW1#vlan database
SW1(vlan)#vtp server #配置VTP角色

SW1(vlan)#vtp domain rex #域名一致才可以同步
SW1(vlan)#vtp password 123 #密码一致才可以同步
SW1(vlan)#exit
APPLY completed.
Exiting....
SW2#vlan database
SW2(vlan)#vtp client
SW2(vlan)#vtp domain rex
SW2(vlan)#vtp password 123
SW2(vlan)#exit
APPLY completed.
Exiting....
SW3与SW2相同
查看VTP
SW1#show vtp status
VTP Version : 2
Configuration Revision : 2 #版本号低的向版本号高的学习
Maximum VLANs supported locally : 256
Number of existing VLANs : 9
VTP Operating Mode : Server
VTP Domain Name : rex
VTP Pruning Mode : Disabled
VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0xA6 0x66 0x1F 0x39 0x33 0x80 0x2F 0x7B
Configuration last modified by 0.0.0.0 at 3-1-02 00:57:51
Local updater ID is 0.0.0.0 (no valid interface found)
VTP裁剪
SW(config)#vtp pruning

创建划分VLAN
在SW1创建vlan其他SW自动同步
SW1#vlan database
SW1(vlan)#vlan 10
VLAN 10 added:
Name: VLAN0010
SW1(vlan)#vlan 20
VLAN 20 added:
Name: VLAN0020
SW1(vlan)#vlan 30
VLAN 30 added:
Name: VLAN0030
SW1(vlan)#exit
APPLY completed.
Exiting....
查看vlan库
SW1#show vlan-sw
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/0, Fa0/1, Fa0/2, Fa0/3
Fa0/4, Fa0/5, Fa0/6, Fa0/7
Fa0/8, Fa0/9, Fa0/10, Fa0/11
Fa0/12, Fa0/13, Fa0/14, Fa0/15
Fa1/0, Fa1/1, Fa1/2, Fa1/3
Fa1/4, Fa1/5, Fa1/6, Fa1/7
Fa1/8, Fa1/9, Fa1/10, Fa1/11
Fa1/12, Fa1/13, Fa1/14, Fa1/15
10 VLAN0010 active
20 VLAN0020 active
30 VLAN0030 active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
划分VLAN
SW2(config)#interface fastEthernet 0/3
SW2(config-if)#sw access vlan 10
SW2(config-if)#exit
其他SW按架构图划分好
查看划分状况
SW2(config)#do show vlan-sw
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/0, Fa0/1, Fa0/2, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa1/0
Fa1/1, Fa1/2, Fa1/3, Fa1/4
Fa1/5, Fa1/6, Fa1/7, Fa1/8
Fa1/9, Fa1/10, Fa1/11, Fa1/12
Fa1/13, Fa1/14, Fa1/15
10 VLAN0010 active Fa0/3
配置trunk
SW1(config)#interface f0/0
SW1(config-if)#sw trunk encapsulation do
SW1(config-if)#sw trunk encapsulation dot1q
SW1(config-if)#sw mode trunk
SW1(config-if)#do show int trun
Port Mode Encapsulation Status Native vlan
Fa0/0 on 802.1q trunking 1
Port Vlans allowed on trunk
Fa0/0 1-1005
Port Vlans allowed and active in management domain
Fa0/0 1,10,20,30
Port Vlans in spanning tree forwarding state and not pruned
Fa0/0 none
其他SW对应一样如此配置trunk
trunk流控技术 —allowed
SW2(config-if)#int f0/0
SW2(config-if)#sw trunk allowed vlan all
其他SW对应一样如此配置trunk
trunk流量优化技术 — native-vlan
native-vlan 流量不打标签,对于不同与本地vlan的直接带原标签转发,设置数据量大的vlan为本地vlan能节省数据包空间,减少链路带宽压力
SW1(config)#interface f0/0
SW1(config-if)#sw trunk native vlan 10
因此SW1与SW2之间native vlan 10,SW2与SW3之间native vlan 20
配置enterchannel
SW2与SW3之间
interface FastEthernet0/1
switchport trunk native vlan 20
switchport mode trunk
channel-group 1 mode on
interface FastEthernet0/2
switchport trunk native vlan 20
switchport mode trunk
channel-group 1 mode on
interface Port-channel1
switchport trunk native vlan 20
switchport mode trunk
先关闭再配置,该channel的vlan配置要与包含的端口一致!否则协议出错,会down
STP配置
STP默认开启
修改对应优先级,内定好阻塞端口从而控制对应VLAN流量走向
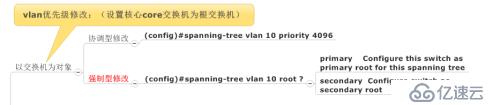
此处采用协调型修改,使SW1成为VLAN10的根交换机,SW3成为VLAN20的根交换机,对于VLAN10阻塞了SW2-SW3,对于VLAN20阻塞了SW2-SW1,从而实现控制流量走向
SW1:spanning-tree vlan 10 priority 4096
SW3:spanning-tree vlan 20 priority 4096
三层通信配置
SW1(config)#ip routing #开启路由功能
SW1(config)#int vlan 10
SW1(config-if)#ip address 192.168.1.254 255.255.255.0
SW1(config-if)#no shut
SW1(config-if)#exit
VLAN20,30参考着配置
DHCP配置
DHCP(config)#int f0/0
DHCP(config-if)#ip add 192.168.3.1 255.255.255.0
DHCP(config-if)#no shut
DHCP(config-if)#exi
DHCP(config)#ip default-gateway 192.168.3.254
DHCP(config)#ip dhcp pool A#配置VLAN10地址池
DHCP(dhcp-config)#network 192.168.1.0 255.255.255.0
DHCP(dhcp-config)#default-router 192.168.1.254
DHCP(dhcp-config)#dns-server 8.8.8.8
DHCP(dhcp-config)#lease 33
DHCP(dhcp-config)#exit
DHCP(config)#ip dhcp pool B ##配置VLAN20地址池
DHCP(dhcp-config)#network 192.168.2.0 255.255.255.0
DHCP(dhcp-config)#default-router 192.168.2.254
DHCP(dhcp-config)#dns-server 8.8.8.8
DHCP(dhcp-config)#lease 33
DHCP(dhcp-config)#exit
DHCP中继配置
SW1(config)#int vlan 10
SW1(config-if)#ip helper-address 192.168.3.1
SW1(config-if)#exit
SW1(config)#int vlan 20
SW1(config-if)#ip helper-address 192.168.3.1
SW1(config-if)#exit
当DHCP请求包到达SW1网关后,根据其VLAN导向对应地址池
port-security配置
在接入口配置!比如SW3的0/3接口
(config)#in f0/1
(config-if)#switchport mode access
(config-if)#switchport port-security //开启端口安全功能
(config-if)#switchport port-security mac-address ? //定义安全MAC表学习方式
H.H.H 48 bit mac address //静态绑定
sticky Configure dynamic secure addresses as sticky //动态学习
(config-if)#switchport port-security maximum 1 //定义安全MAC表存储条目数量为1
(config-if)#switchport port-security violation ? //定义惩罚模式
protect Security violation protect mode //丢弃非法流量
restrict Security violation restrict mode //丢弃非法流量并发送报警信息
shutdown Security violation shutdown mode //丢弃非法流量并把此接口软关闭
自动恢复
errdisable recovery cause(原因)里面选 bpduguard
err recovery interval 30// 默认300秒后接口自动恢复
查看命令:
show port-security address
show port-security interface f0/1
由于时间和篇幅有限,对于知识相关概念描述不多,而且对相关配置有一点点省略,如果读者在模拟实验过程中有任何疑问欢迎留言!
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。