您好,登录后才能下订单哦!
ASA 5520内网端口互访实验
测试如何实现ASA5520不同内网端口同时安全级别不一样额内网端口间的
互访配置。
测试如何实现ASA5520不同内网端口但是相同安全级别间的端口的互访。
实验环境:基于GNS3的虚拟环境,ASA版本为8.4(2)
试验拓扑:
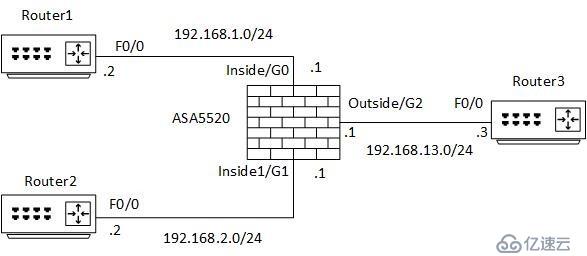
Router1 基本配置:
ip domain name test.com
username root secret 5 $1$/3e0$pTshnFze2RSAvILS1t6Ak/
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
interface FastEthernet0/0
ip address 192.168.1.2 255.255.255.0
duplex half
ip route 0.0.0.0 0.0.0.0 192.168.1.1
Router2基本配置
ip domain name test.com
username root password 0 root
interface Loopback0
ip address 2.2.2.2 255.255.255.0
!
interface FastEthernet0/0
ip address 192.168.2.2 255.255.255.0
duplex half
ip route 0.0.0.0 0.0.0.0 192.168.2.1
line vty 0 4
login local
transport input telnet ssh
Router3基本配置:
interface FastEthernet0/0
ip address 192.168.13.3 255.255.255.0
duplex half
ip route 0.0.0.0 0.0.0.0 192.168.13.1
ASA5520基本配置:
interface GigabitEthernet0
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1
nameif inside1
security-level 90
ip address 192.168.2.1 255.255.255.0
!
interface GigabitEthernet2
nameif outside
security-level 0
ip address 192.168.13.1 255.255.255.0
route outside 0.0.0.0 0.0.0.0 192.168.13.3 1
route inside 1.1.1.0 255.255.255.0 192.168.1.2 1
route inside1 2.2.2.0 255.255.255.0 192.168.2.2 1
测试<一>:
1 分别从router1和router2 PING Router3的地址:
R1#ping 192.168.13.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.13.3, timeout is 2 seconds:
.....Success rate is 0 percent (0/5)
R2#ping 192.168.13.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.13.3, timeout is 2 seconds:
.....Success rate is 0 percent (0/5)
2 分别从router1和router2 telnet Router3的地址:
R1#192.168.13.3
Trying 192.168.13.3 ... Open
User Access Verification
Username: root
Password:
R3>
R2#192.168.13.3
Trying 192.168.13.3 ... Open
User Access Verification
Username: root
Password:
R3>
结论:默认情况下,从高安全级别端口的网络可以访问低安全级别的网络,但是PING协议默认禁止,需要另外打开,打开命令如下:
access-list outside permit icmp any any
access-group outside in interface outside
此时从 inside和inside1端口都可以PING通Router3的端口地址:
R1#ping 192.168.13.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.13.3, timeout is 2 seconds:
!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 32/70/144 ms
R2#ping 192.168.13.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.13.3, timeout is 2 seconds:
!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 12/50/132 ms
测试<二>:
1 从Router1 ping和telnet到Router2端口的地址:
R1#ping 192.168.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.2, timeout is 2 seconds:
.....Success rate is 0 percent (0/5)
R1#192.168.2.2
Trying 192.168.2.2 ... Open
User Access Verification
Username: root
Password:
R2>
Ping不通,但是telnet可以访问,这是因为inside端口的网络安全级别高于inside1的网络安全级别,因此虽然ping默认不通,但是telnet就没有问题,符合测试一的结论。
我们添加命令让PING可以通过:
access-list inside1 permit icmp any any
access-group inside1 in interface inside1
R1#ping 192.168.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.2, timeout is 2 seconds:
!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 32/65/136 ms
为了能让低级别的inside1访问高级别的inside,我们需要添加如下命令:
access-list inside1 extended permit tcp host 192.168.2.2 host 192.168.1.2 eq telnet log
access-list inside1 extended permit tcp host 192.168.2.2 host 192.168.1.2 eq ssh log
access-group inside1 in interface inside1
此时再测试:
R2#telnet 192.168.1.2
Trying 192.168.1.2 ... Open
User Access Verification
Username: root
Password:
R1>exit
[Connection to 192.168.1.2 closed by foreign host]
R2#ssh -l root 192.168.1.2
Password:
R1>
发现从低级别的inside1已经可以访问高级别的inside。
结论:在内网安全级别不同的端口间访问时,从高级别安全端口访问低级别安全端口除了PING默认禁止,其余服务都可以访问,从低级别端口访问到高级别端口时,需要启用访问列表并应用在低级别端口的IN方向上。
测试<三>:不同内网端口但是相同安全级别间的端口的互访
删除前面配置的访问列表,把inside和inside1配置成相同的安全级别100:
interface GigabitEthernet0
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1
nameif inside1
security-level 100
ip address 192.168.2.1 255.255.255.0
此时在R1上测试:
R1#ping 192.168.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.2, timeout is 2 seconds:
.....Success rate is 0 percent (0/5)
R1# 192.168.2.2
Trying 192.168.2.2 ...% Connection timed out; remote host not responding
都是不通的,在R2上测试也是一样的,不通。
加上命令:same-security-traffic permit inter-interface,继续在R1上测试:
R1#ping 192.168.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.2, timeout is 2 seconds:
!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 28/95/240 ms
R1# 192.168.2.2
Trying 192.168.2.2 ... Open
User Access Verification
Username: root
Password:
R2>
可以看到访问完全没有任何问题:
结论:在相同安全级别间的访问,只需要使用命令就能实现。
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。