您好,登录后才能下订单哦!
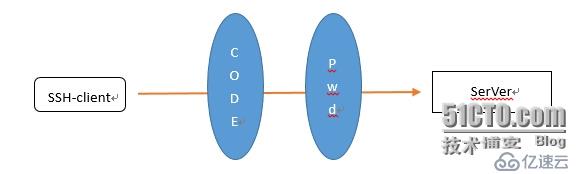
基本的原理如上图:
客户端在输入code码之后,才可以输入服务器的密码,进行账户验证,方可进入服务器。
实现方式如下:
1. 安装所需组件
# yum -y install mercurial pam-devel
2. 安装qrencode,在Linux上,有一个名为 QrenCode 的命令行工具可以很容易帮我们生成二维码,google authenticator命令行生成二维码就是调用它。
# wgethttp://fukuchi.org/works/qrencode/qrencode-3.3.1.tar.gz
# tar zxfqrencode-3.3.1.tar.gz
# cdqrencode-3.3.1
# ./configure--prefix=/usr && make && make install
3. 安装GoogleAuthenticator
# wget --no-check-certificate https://google-authenticator.googlecode.com/files/libpam-google-authenticator-1.0-source.tar.bz2
# tar jxvf libpam-google-authenticator-1.0-source.tar.bz2
# cd libpam-google-authenticator-1.0
# make && make install
4. SSH登录时调用google-authenticator模块
vim /etc/pam.d/sshd
在第一行添加如下:
auth required pam_google_authenticator.so
vim /etc/ssh/sshd_config
ChallengeResponseAuthenticationyes #开启此行
UsePAM yes #添加此行
Service sshd restart
5. 生成google-authenticator配置
google-authenticator
Do youwant authentication tokens to be time-based (y/n) y
https://www.google.com/chart?chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/root@node3.mengtao.com%3Fsecret%3DABEXG5K6CVB56BXY
#此网址为生成的二维码,客户端扫描
Your newsecret key is:node3.mengtao.com
Yourverification code is 582849
Youremergency scratch codes are:
30776626
14200155
80795568
23936997
21919909
#上面几行数字为应急码
Do youwant me to update your "/root/.google_authenticator" file (y/n) y
#更新配置文件
Do youwant to disallow multiple uses of the same authentication
token?This restricts you to one login about every 30s, but it increases
yourchances to notice or even prevent man-in-the-middle attacks (y/n) y
#禁止一个口令多用
Bydefault, tokens are good for 30 seconds and in order to compensate for
possibletime-skew between the client and the server, we allow an extra
tokenbefore and after the current time. If you experience problems with poor
timesynchronization, you can increase the window from its default
size of1:30min to about 4min. Do you want to do so (y/n) n
#客户端与服务器时间误差
If thecomputer that you are logging into isn't hardened against brute-force
loginattempts, you can enable rate-limiting for the authentication module.
Bydefault, this limits attackers to no more than 3 login attempts every 30s.
Do youwant to enable rate-limiting (y/n) y
#次数限制
在设备上输入序列码和扫描二维码都可以
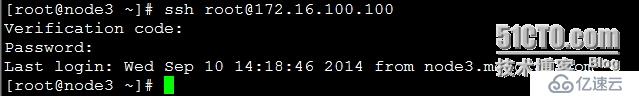
6. 登录验证
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。