您好,登录后才能下订单哦!
ipsec简介
IPSec(InternetProtocolSecurity)是安全联网的长期方向。它通过端对端的安全性来提供主动的保护以防止专用网络与 Internet 的***。在通信中,只有发送方和接收方才是唯一必须了解 IPSec 保护的计算机。在 Windows 2000、Windows XP 和 Windows Server 2003 家族中,IPSec 提供了一种能力,以保护工作组、局域网计算机、域客户端和服务器、分支机构(物理上为远程机构)、Extranet 以及漫游客户端之间的通信。
下面我们就用一台三层交换机和三台防火墙来模拟一下ipsec
拓扑图
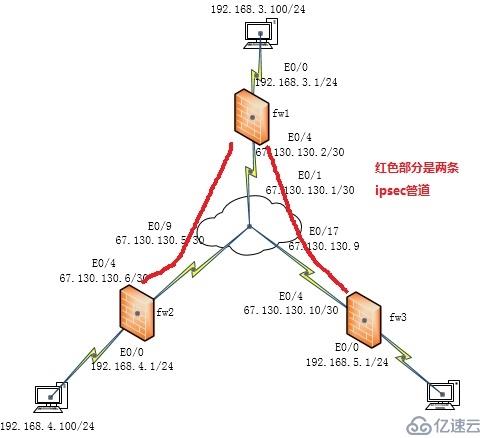
设置三层交换机
<Quidway>sys
[Quidway]sys isp
[isp]vlan 10
[isp-vlan10]port e0/1
[isp-vlan10]vlan 20
[isp-vlan20]port e0/9
[isp-vlan20]vlan 30
[isp-vlan30]port e0/17
[isp-vlan30]int vlan10
[isp-Vlan-interface10]ip add 67.130.130.1 255.255.255.252
[isp-Vlan-interface10]int vlan 20
[isp-Vlan-interface20]ip add 67.130.130.5 255.255.255.252
[isp-Vlan-interface20]int vlan 30
[isp-Vlan-interface30]ip add 67.130.130.9 255.255.255.252
设置fw1
<H3C>sys
[H3C]sys fw1
[fw1]int eth0/0
[fw1-Ethernet0/0]ip add 192.168.3.1 24
[fw1-Ethernet0/0]loopback
[fw1-Ethernet0/0]int eth0/4
[fw1-Ethernet0/4]ip add 67.130.130.2 30
取消端口隔离
[fw1]undo insulate
添加eth0/4到untrust
[fw1]firewall zone untrust
[fw1-zone-untrust]add int eth0/4
添加eth0/0到trust
[fw1]firewall zone trust
[fw1-zone-trust]add int eth0/0
用访问控制列表筛选
[fw1]acl number 3000 match-order auto
[fw1-acl-adv-3000]rule 10 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.4.0 0.0.0.255
[fw1-acl-adv-3000]rule 20 deny ip source any destination any
创建安全提议tran1
[fw1]ipsec proposal tran1
选择管道方式
[fw1-ipsec-proposal-tran1]encapsulation-mode tunnel
选择安全协议sep
[fw1-ipsec-proposal-tran1]transform esp
完整性校验选md5
[fw1-ipsec-proposal-tran1]esp authentication-algorithm md5
加密算法选des
[fw1-ipsec-proposal-tran1]esp encryption-algorithm des
设置ike peer
[fw1]ike peer fw2
设置来源ip
[fw1-ike-peer-fw2]local-address 67.130.130.2
设置目标ip
[fw1-ike-peer-fw2]remote-address 67.130.130.6
设置密钥
[fw1-ike-peer-fw2]pre-shared-key 123456
注意,这个密钥一定要记住,下面还要用到
isa和筛选流相结合
选择动态isa
[fw1]ipsec policy policy1 10 isakmp
筛选符合3000表的流
[fw1-ipsec-policy-isakmp-policy1-10]security acl 3000
选择符合提议tran1的
[fw1-ipsec-policy-isakmp-policy1-10]proposal tran1
选择ike 对等体为fw2
[fw1-ipsec-policy-isakmp-policy1-10]ike-peer fw2
进入端口eth0/4应用策略
[fw1]int eth0/4
[fw1-Ethernet0/4]ipsec policy policy1
第一条隧道已经设置好了,接着该去设置这条隧道的另一端,进入防火墙fw2
下面是第二条隧道的设置
[fw1]acl number 3001 match-order auto
[fw1-acl-adv-3001]rule permit ip source 192.168.3.0 0.0.0.255 destination 192.168.5.0 0.0.0.255
[fw1-acl-adv-3001]rule deny ip source any destination any
[fw1]ipsec proposal tran2
[fw1-ipsec-proposal-tran2]encapsulation-mode tunnel
[fw1-ipsec-proposal-tran2]transform esp
[fw1-ipsec-proposal-tran2]esp authentication-algorithm md5
[fw1-ipsec-proposal-tran2]esp encryption-algorithm des
[fw1]ike peer fw3
[fw1-ike-peer-fw3]local-address 67.130.130.2
[fw1-ike-peer-fw3]remote-address 67.130.130.10
[fw1-ike-peer-fw3]pre-shared-key 654321
[fw1]acl number 3001 match-order auto
[fw1-acl-adv-3000]undo rule 20
设置fw2
<H3C>sys
[H3C]sys fw2
[fw2]int eth0/0
[fw2-Ethernet0/0]ip add 192.168.4.1 24
[fw2-Ethernet0/0]loopback
[fw2-Ethernet0/0]int eth0/4
[fw2-Ethernet0/4]ip add 67.130.130.6 30
[fw2]undo insulate
[fw2]firewall packet-filter default permit
[fw2]firewall zone trust
[fw2-zone-trust]add interface eth0/0
[fw2]firewall zone untrust
[fw2-zone-untrust]add int eth0/4
[fw2]ip route-static 0.0.0.0 0 67.130.130.5
[fw2]acl number 3000 match-order auto
[fw2-acl-adv-3000]rule 10 permit ip source 192.168.4.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
[fw2-acl-adv-3000]rule 20 deny ip source any destination any
[fw2]ipsec proposal tran1
[fw2-ipsec-proposal-tran1]encapsulation-mode tunnel
[fw2-ipsec-proposal-tran1]esp authentication-algorithm md5
[fw2-ipsec-proposal-tran1]esp encryption-algorithm des
[fw2]ike peer fw1
[fw2-ike-peer-fw1]local-address 67.130.130.6
[fw2-ike-peer-fw1]remote-address 67.130.130.2
[fw2-ike-peer-fw1]pre-shared-key 123456
这个密钥要和另外一端的一样
[fw2]ipsec policy policy1 10 isakmp
[fw2-ipsec-policy-isakmp-policy1-10]security acl 3000
[fw2-ipsec-policy-isakmp-policy1-10]proposal tran1
[fw2-ipsec-policy-isakmp-policy1-10]ike-peer fw1
[fw2]int eth0/4
[fw2-Ethernet0/4]ipsec policy policy1
配置fw3
<H3C>sys
[H3C]sys fw3
[fw3]int eth0/0
[fw3-Ethernet0/0]ip add 192.168.5.1 24
[fw3-Ethernet0/0]loopback
[fw3-Ethernet0/0]int eth0/4
[fw3-Ethernet0/4]ip add 67.130.130.10 30
[fw3]undo insulate
[fw3]firewall zone untrust
[fw3-zone-untrust]add int eth0/4
[fw3]firewall zone trust
[fw3-zone-trust]add int eth0/0
[fw3]ip route-static 0.0.0.0 0 67.130.130.9
[fw3]acl number 3001 match-order auto
[fw3-acl-adv-3001]rule 10 permit ip source 192.168.5.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
[fw3-acl-adv-3001]rule 20 deny ip source any destination any
[fw3]ipsec proposal tran2
[fw3-ipsec-proposal-tran2]encapsulation-mode tunnel
[fw3-ipsec-proposal-tran2]transform esp
[fw3-ipsec-proposal-tran2]esp authentication-algorithm md5
[fw3-ipsec-proposal-tran2]esp encryption-algorithm des
[fw3]ike peer fw1
[fw3-ike-peer-fw1]local-address 67.130.130.10
[fw3-ike-peer-fw1]remote-address 67.130.130.2
[fw3-ike-peer-fw1]pre-shared-key 654321
[fw3]ipsec policy policy1 10 isakmp
[fw3-ipsec-policy-isakmp-policy1-10]security acl 3001
[fw3-ipsec-policy-isakmp-policy1-10]tracert tran2
[fw3-ipsec-policy-isakmp-policy1-10]ike-peer fw1
[fw3]int eth0/4
[fw3-Ethernet0/4]ipsec policy policy1
好了ipsec
免责声明:本站发布的内容(图片、视频和文字)以原创、转载和分享为主,文章观点不代表本网站立场,如果涉及侵权请联系站长邮箱:is@yisu.com进行举报,并提供相关证据,一经查实,将立刻删除涉嫌侵权内容。